Using Federated Machine Learning to Overcome the AI Scale Disadvantage

When it comes to scaling AI, the central advantage Big Tech has over its SMB counterparts is access to massive amounts of data—think Facebook or Amazon. Here’s how SMBs can catch up:
Amazon’s Cloud Business Has Its Challengers. Analysts Think AI Is Key to Staying Dominant

Experts are bullish on Amazon’s headlong plunge into AI—but many questions remain and AI’s integration into #cloudtech is rife with unknowns and potential pitfalls.
What Is ai-powered Behavioral Analysis in Cybersecurity
Leveraging artificial intelligence to learn and predict malicious behavior patterns, #AIbehavioralanalysis is an increasingly potent tool in the fight against the world’s most dangerous cybercriminals.
How Enterprise Sales Can Supercharge Product-Led Growth

Product-led growth (#PLG) is proving to be a highly effective startup strategy. Here’s a blueprint for making it work for your organization.
Crash Course in Microsoft Purview

AI is improving cybersecurity by identifying and blocking threats early. But AI is also a tool for cybercriminals. Knowledge is power. 💪 Download and read the latest #AI threat intelligence from @Microsoft Security. 👉
What’s new in Azure Data, AI, and Digital Applications: Are you ready to go from GenAI experimentation to solutions at scale?

When are you going to get serious about implementing AI? Mañana? Could be too late. But no worries. @Microsoft has a solution. Many, in fact. Check out this blog article for details about how Microsoft’s latest Azure Data, AI and Digital Applications can take you from GenAI experimentation to solutions deployed at scale – and deliver a substantial ROI. DM us to get started and move forward into an AI future.
Remote Work Is Here to Stay. Remote Workers Need Better Internet

Remote work won’t be fully optimized until remote workers have access to the same networking power as their in-person counterparts. Good analysis:
Managed Risk and Threat Assessments

Are you aware of your current cybersecurity strengths and weaknesses? Let @Gradient Cyber conduct a full assessment of your IT environment, including networks and endpoints. Contact QuattroOne to find out how the power of Gradient Cyber Managed Risk Assessments can take your organization’s cybersecurity initiatives to the next level.
A free consultation on dodging AI pitfalls

The fact that AI can help take your organization to the next level shouldn’t obscure the tech’s many pitfalls. Schedule a free consultation to go over the most common #AIobstacles to watch out for.
Streamline your cloud ops with AI—free demo

Our new AI-powered solution can streamline your #cloudoperations, boosting productivity and reducing costs. Schedule a free demo to see it in action.
Demo an AI-powered cybersecurity solution

Sign up for a free demo to see how our #AIpowered cybersecurity solution can automate incident response, detect and remediate threats faster, and significantly improve your security posture.
Assess your tech portfolio—free consultation

Is your current tech portfolio optimized for advancing your business goals? Schedule a free consultation with one of our experts to assess if you have too few—or too many—tech solutions.
Overcome hybrid work challenges—free demo

Ready to transform your #hybridwork environment by streamlining collaboration between remote and in-person employees? We have the solution to make it happen. Schedule a free demo to learn more.
Extended Detection and Response (XDR)

IT teams have enough on their plate managing day-to-day IT tasks. Asking them to also oversee the increasingly complex cybersecurity landscape isn’t viable for many SMBs—both from an operational and budgetary standpoint. Read the datasheet to learn how @Gradient Cyber can provide 24/7 threat detection and response for your entire IT infrastructure—freeing up your IT team to innovate and handle business critical tasks.
Digital Transformation Solutions for Retail

Don’t miss this webinar on digital transformation solutions for retail by #Samsung! 💡 Follow this link to sign up! 🤝 You’ll discover how to deploy digital signage to engage consumers, transform the customer journey, and drive sales. If you’d like additional details about Samsung technology for retail, contact QuattroOne.
LG Cloud Device – CQ600 USP Film

Introducing the #LG Cloud Device Desktop Thin Client CQ600! ✨ Need a virtual desktop solution? Watch this video to learn more about this endpoint. 💡 If you have questions, QuattroOne is here to help.
5 Must-Have Technologies for a Brand-New Business

If you’re running a brand-new business, you need a customer relationship management system, project management software, online data storage, financial management tools, and cybersecurity software. Read this article to learn more. To learn about SMB solutions and services that are ideal for your company, contact us today.
Smart Tactics to Reduce Cloud Waste at Your Business

Cloud computing has revolutionized the way businesses operate. It offers scalability, flexibility, and cost-efficiency. But cloud services also come with a downside: cloud waste. Cloud waste is the unnecessary spending of resources and money on cloud services. These services are often not fully utilized or optimized. About 32% of cloud spending is wasted. This can […]
Get started with Microsoft Copilot with Graph-grounded chat in Microsoft Teams
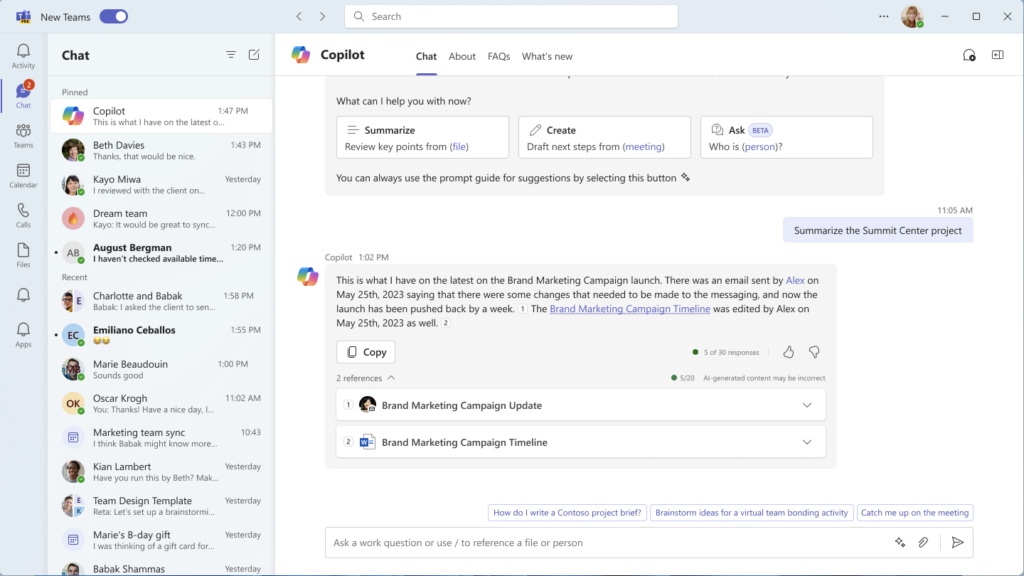
@Microsoft Copilot can help you find information, dig up lost Chat messages and organize your notes. Learn how #Copilot can help you be more productive in this article. 👉
How to minimize data risk for generative AI and LLMs in the enterprise
Data is the catalyst for AI efficacy. And the risk of exposing sensitive data in the rush to improve AI models has never been greater. Important read 👇


